What Is a Self Encrypting SSD? Worry About DATA Privacy?

If you’re like most people, you probably don’t think about your data security until it’s too late. You store all of your important documents on your computer, and you don’t give a second thought to the possibility that someone could access them if they got their hands on your device.
This is where self encrypting SSDs can help. These drives encrypt all of your data automatically, so even if someone manages to get their hands on your device, they won’t be able to access any of your information without the proper password. If you’re interested in learning more about self-encrypting SSDs, keep reading!
In summary, self encrypting SSD is a type of drive that is able to encrypt its own data. when data is written to the drive, it is automatically encrypted (at the hardware level). This provides an extra layer of security in case the drive is ever lost or stolen.
What is Data Encryption?

Data encryption is a process of transforming readable data into an unreadable format. This is done using an algorithm and a key. The data can only be decrypted and read by someone who has access to the key.
This ensures that only authorized individuals can access the information, and helps to prevent cyber criminals from stealing sensitive data. Data encryption is used by businesses of all sizes to protect customer information, financial records, and other confidential data.
In many cases, data encryption is required by law in order to meet industry regulations. When implemented properly, data encryption is an effective way to protect important information from unauthorized access.
There are several different types of data encryption, each with its own strengths and weaknesses.
- Asymmetric encryption
- Symmetric encryption
Types of Data Encryption
1) Asymmetric Encryption
Asymmetric encryption, also known as public-key encryption, is a type of cryptography that uses pairs of keys to encrypt and decrypt data. One key, known as the public key, is used to encrypt information, while the other key, known as the private key, is used to decrypt it.
The major advantage of asymmetric encryption is that it offers a higher level of security than symmetric encryption, which uses a single key for both encryption and decryption. With asymmetric encryption, even if an attacker manages to obtain the public key, they will not be able to decrypt information unless they also have the private key. As a result, asymmetric encryption is often used for applications where security is critical, such as online banking and communication.
RSA and ECC are two of the most popular algorithms used for asymmetric encryption.
2) Symmetric Encryption
Symmetric encryption, also known as private key encryption, is a type of cryptography where the same key is used to encrypt and decrypt data. This key is usually a secret shared between the sender and the receiver of the message. In order for symmetric encryption to be effective, both the sender and receiver must have a copy of the key and keep it secure.
One downside of symmetric encryption is that if the key is lost or stolen, then the data cannot be decrypted. As a result, it is important to have a backup key or use a different type of encryption if possible. As a result, symmetric encryption is often used in conjunction with other types of cryptography, such as public key encryption, which provides an additional layer of security.
There are hundreds of symmetric key algorithms in existence, though the most common encryption methods include
- AES,
- RC4,
- DES,
- 3DES,
- RC5,
- RC6,
- QUAD etc..
Each algorithm has its own strengths and weaknesses, so choosing the right one for a given situation is essential. For example, AES is considered to be very secure, but it can be slower than other algorithms. On the other hand, RC4 is much faster but has been shown to be less secure than AES.
DES and 3DES are both fairly old algorithms that are no longer considered to be as secure as newer options, but they may still be suitable for some situations. Ultimately, the choice of algorithm depends on the particular needs of the situation.
Software Encryption vs Hardware Encryption
Encryption can be performed at the software level or hardware level. Software encryption is typically performed by the computer’s operating system using a built-in encryption tool. Hardware encryption, on the other hand, is performed at the hardware level.
1) Software Encryption
While encryption is a powerful tool for protecting data, it is important to be aware of its limitations. One potential drawback of software encryption is that it can place a heavy burden on processor resources. In order to encrypt and decrypt data, the processor must perform complex mathematical operations, which can slow down other tasks. Additionally, if a software encryption system is not properly implemented, it may be possible to recover the data that has been encrypted.
2) Hardware Encryption
Hardware encryption uses a dedicated chip, rather than software, to encrypt and decrypt data. This allows for real-time encryption and decryption of data, without requiring the CPU to be involved in the process. Because hardware encryption is not reliant on software, it is less susceptible to attack. In addition, hardware encryption can provide better performance than software encryption, as it does not require the CPU to be involved in the process.
So more secure method of keeping your data safe is to encrypt it on a hardware level. If your SSD drive includes an encryption controller that supports 256-bit AES encryption, you can use full disk encryption, which is also referred to as a self-encrypting drive.
What is a Self-Encrypting Drive (SED)?
A self-encrypting drive (SED) is a type of hard disk drive (HDD) or solid-state drive (SSD) that has an encryption circuit built into it. This circuit encrypts all data on the drive automatically, without any user intervention. SEDs are often used in laptops and other devices where data security is a concern.
For example, if a laptop with a SED is lost or stolen, the data on the drive will be protected from unauthorized access. SEDs are also used in some enterprise storage systems to protect sensitive data. One advantage of SEDs is that they do not require any special software or drivers to work; they can be used with any operating system.
Another advantage is that they provide full-disk encryption, meaning that all data on the drive is encrypted, not just selected files or folders. A disadvantage of SEDs is that they tend to be more expensive than regular HDDs or SSDs.
What Encryption Method Is Used by SSD?
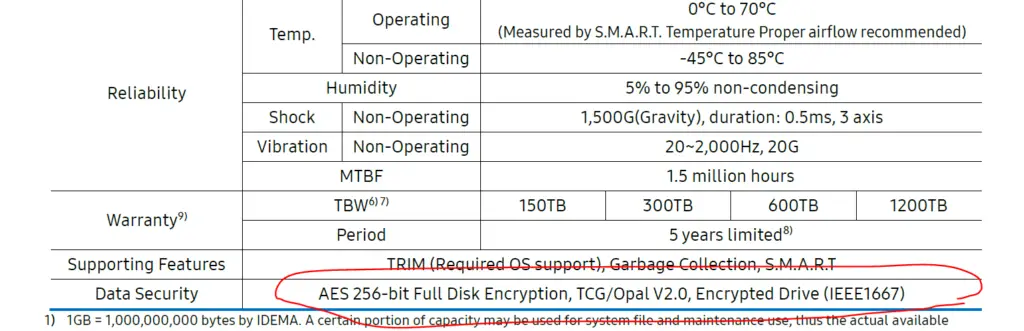
Modern encrypted SSDs use a AES 256 bit hardware based encryption. Note that SSD has a special controller (AES encryption chip) which does this at the hardware level so the encryption process won’t slow down. The encryption process is designed to be extremely difficult to break, even for powerful computers.
To know more about OPAL V2 standard (Highlighted in the above image) read further.
As a result, encrypted SSDs are a very effective way to protect data from being accessed by unauthorized individuals. However, it is important to note that encrypted SSDs can still be damaged or destroyed, just like any other type of storage device. As such, they should be treated with care and stored in a safe location.

If you are interested in Samsung 970 EVO plus SSD features refer to my article Samsung 970 EVO Plus vs 980: Which is Best?

How Does AES Disk Encryption Work on SSD?
The encryption key is a 256-bit number generated randomly and stored in an encrypted format on a hidden area of the drive. The Encryption Key never leaves the device. Not even the drive manufacturer knows the value of the Encryption Key, assuming that AES 256-bit encryption is used.
The second key is the Authorization Key, which the user sets and authorizes access to the drive. If not set, like when first using the drive, it will appear as a regular unencrypted SSD. So, the user must set a password in order to encrypt and decrypt data on-the-fly.
The process of encrypting and decrypting data is completely transparent to the user. That is, data is automatically encrypted right before it is written to the drive and decrypted when read back from the drive all in real-time and on the fly, without any user intervention.
The key here is that the data is encrypted at the hardware level and not at the software level. This means that a self-encrypting SSD will work with any operating system (OS) and does not require special drivers or encryption software. The drive will appear and function just like a regular SSD.
How To Manage An Encrypt SSD?
If the requirements of your drive and host system are compatible, you can use
- ATA security
- TCG Opal 2.0 software
to manage an encrypted SSD.
1) ATA security (ATA Secure Command Set)
The Authentication Key can be set by creating an ATA password, which will enable authentication on encrypted SSDs. ATA security is a protocol that helps to protect data on ATA-compatible devices, such as hard drives and SSDs.
One of the key features of ATA security is the Authentication Key, which is used to encrypt and decrypt data. The Authentication Key can be set by creating an ATA password, which will enable authentication on encrypted SSDs. You can also use the ATA interface to destroy all data on a disk. By using ATA security, you can help to keep your data safe from unauthorized access.
2) TCG OPAL 2.0 software
The Trusted Computing Group (TCG) has developed a new specification, OPAL 2.0, which defines a standard interface for SSDs. This allows for better management of SSDs, as well as stronger authentication and encryption.
In addition, OPAL 2.0-compliant SSDs are designed to minimize write amplification, which can improve the performance and longevity of the drive. As more and more manufacturers adopt the OPAL 2.0 specification, it is likely that SSDs will become even more popular in the coming years. If an SSD supports this specification you can see it in the manual.
Why Should You Buy an Encrypted SSD?
These days, data security is more important than ever. With hackers becoming more sophisticated and data breaches making headlines on a regular basis, it’s crucial to take steps to protect your information. One way to do this is by investing in an encrypted SSD.
This means that if your SSD falls into the wrong hands, your data will be safe. Encryption adds an extra layer of security, making it more difficult for hackers to access your information. If you’re looking for peace of mind, an encrypted SSD is a wise investment.

